As organizations increasingly migrate to the cloud, ensuring the security of cloud environments becomes paramount. A comprehensive cloud security assessment is essential for identifying vulnerabilities, mitigating risks, and ensuring compliance with industry standards. This guide provides an in-depth look at conducting a cloud security assessment, including specific approaches for AWS and Azure, essential tools, and methodologies.
Understanding Cloud Security Assessment
A cloud security assessment evaluates the security posture of your cloud environment. It involves identifying potential vulnerabilities, assessing security controls, and ensuring compliance with regulatory requirements. The goal is to provide a clear understanding of the security risks and the effectiveness of existing security measures.
Key Components of a Cloud Security Assessment:
- Risk Identification: Identifying potential threats and vulnerabilities.
- Control Evaluation: Assessing the effectiveness of security controls.
- Compliance Verification: Ensuring adherence to regulatory requirements.
- Recommendations: Providing actionable steps to mitigate identified risks.
AWS Cloud Security Assessment
AWS (Amazon Web Services) is one of the leading cloud service providers, offering a range of security features. An AWS cloud security assessment focuses on evaluating the security of AWS environments, including configurations, access controls, and compliance.
Conducting an AWS Cloud Security Assessment
- AWS Cloud Security Assessment Questionnaire: Start by using an AWS-specific questionnaire to gather information about your environment. This includes details on configurations, access controls, and data protection measures.
- Security Best Practices: Assess your environment against AWS security best practices, such as the AWS Well-Architected Framework.
- Configuration Review: Evaluate the configuration of AWS services, ensuring that they follow security best practices.
- Access Control: Review IAM (Identity and Access Management) policies to ensure that access controls are appropriately implemented.
- Compliance Check: Verify compliance with relevant regulatory standards, such as GDPR, HIPAA, and PCI DSS.
AWS Cloud Security Assessment Tools
- AWS Trusted Advisor: Provides real-time recommendations to help you follow AWS best practices.
- AWS Security Hub: Centralizes security alerts and compliance status across AWS accounts.
- AWS Config: Continuously monitors and records AWS resource configurations to help you assess compliance.
Azure Cloud Security Assessment
Azure, Microsoft’s cloud platform, offers robust security features and services. An Azure cloud security assessment involves evaluating the security posture of Azure environments, including configurations, access controls, and compliance.
Conducting an Azure Cloud Security Assessment
- Azure Cloud Security Assessment Questionnaire: Use an Azure-specific questionnaire to gather information about your environment. This includes details on configurations, access controls, and data protection measures.
- Security Best Practices: Assess your environment against Azure security best practices, such as the Microsoft Azure Well-Architected Framework.
- Configuration Review: Evaluate the configuration of Azure services to ensure they follow security best practices.
- Access Control: Review Azure Active Directory (AD) policies to ensure appropriate access controls.
- Compliance Check: Verify compliance with relevant regulatory standards, such as GDPR, HIPAA, and PCI DSS.
Azure Cloud Security Assessment Tools
- Azure Security Center: Provides unified security management and advanced threat protection across hybrid cloud workloads.
- Azure Policy: Helps enforce organizational standards and assess compliance at scale.
- Azure Advisor: Offers personalized best practices recommendations to optimize your Azure deployments.
Cloud Security Assessment Questionnaire
A cloud security assessment questionnaire is a crucial tool for gathering detailed information about your cloud environment. It helps identify potential vulnerabilities and assess the effectiveness of security controls.
Key Sections of a Cloud Security Assessment Questionnaire:
- General Information: Details about the cloud environment, including the provider, services used, and architecture.
- Access Control: Information about identity management, authentication methods, and access policies.
- Data Protection: Details on data encryption, storage, and transmission security measures.
- Configuration Management: Information about resource configurations and management practices.
- Compliance: Details on adherence to regulatory requirements and industry standards.
- Incident Response: Information about incident detection, response, and recovery processes.
Example Questions:
- How are user identities managed and authenticated?
- What encryption methods are used for data at rest and in transit?
- How are configurations monitored and managed?
- What are the compliance requirements, and how are they met?
- What is the process for detecting and responding to security incidents?
Cloud Security Assessment Service
Engaging a professional cloud security assessment service can provide an in-depth evaluation of your cloud environment’s security posture. These services offer expertise, tools, and methodologies to identify vulnerabilities and recommend mitigation strategies.
Benefits of Cloud Security Assessment Services
- Expertise: Access to security experts with specialized knowledge in cloud security.
- Comprehensive Analysis: Detailed assessment covering all aspects of cloud security.
- Actionable Insights: Recommendations for improving security posture and mitigating risks.
- Compliance Assurance: Verification of compliance with regulatory standards and industry best practices.
Choosing a Cloud Security Assessment Service
- Reputation: Choose a service provider with a strong reputation and positive reviews.
- Experience: Look for providers with experience in assessing environments similar to yours.
- Comprehensive Approach: Ensure the service covers all aspects of cloud security, including configurations, access controls, and compliance.
- Customized Solutions: Select a provider that offers tailored solutions to meet your specific needs.
Cloud Security Assessment Approach
A structured approach to cloud security assessment ensures a thorough and effective evaluation of your cloud environment’s security posture.
Key Steps in a Cloud Security Assessment Approach:
- Preparation: Define the scope, objectives, and methodology of the assessment.
- Data Collection: Gather information using questionnaires, tools, and interviews.
- Analysis: Analyze the collected data to identify vulnerabilities and assess security controls.
- Evaluation: Compare the findings against best practices and regulatory requirements.
- Reporting: Document the findings in a comprehensive cloud security assessment report.
- Recommendations: Provide actionable recommendations to address identified risks.
- Follow-Up: Monitor the implementation of recommendations and conduct periodic reassessments.
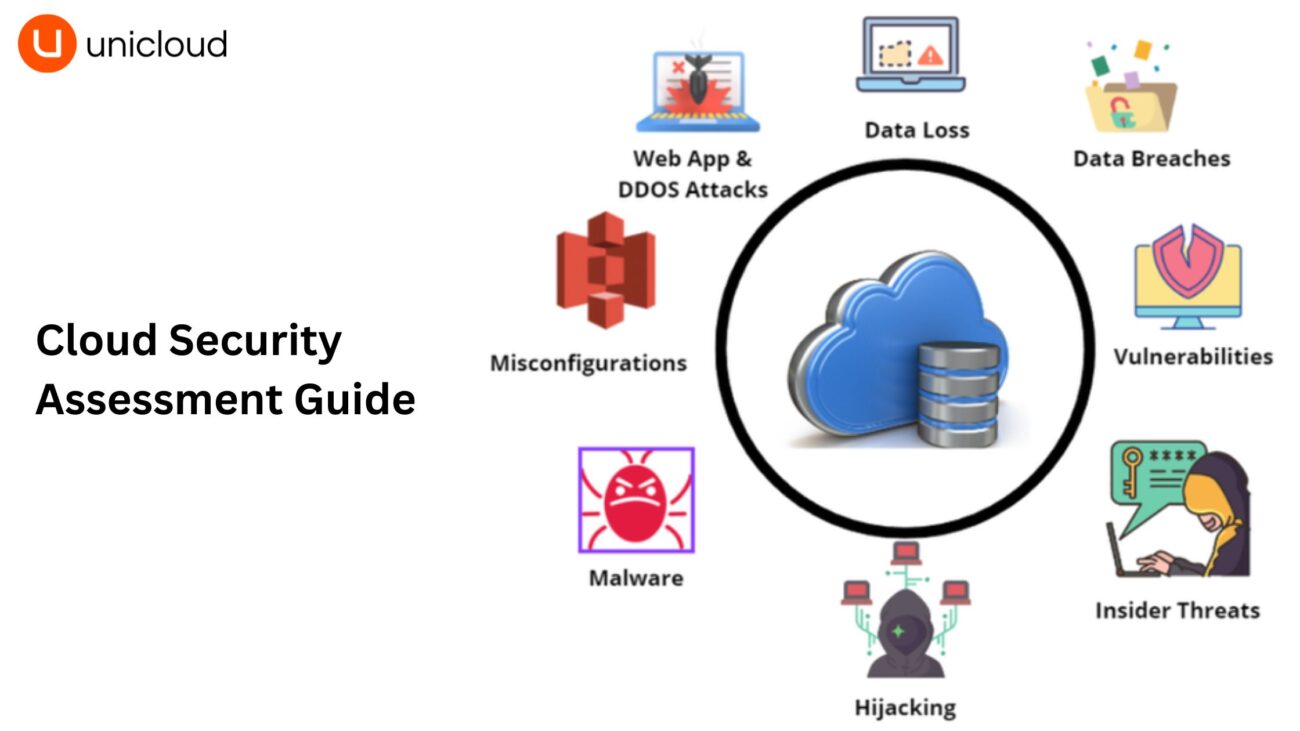
Assessing the Security Risks of Cloud Computing
Assessing the security risks of cloud computing involves identifying potential threats and vulnerabilities that could impact your cloud environment.
Common Security Risks in Cloud Computing:
- Data Breaches: Unauthorized access to sensitive data.
- Misconfigurations: Incorrect settings that expose resources to security threats.
- Insider Threats: Malicious or negligent actions by employees or contractors.
- Denial of Service (DoS): Attacks that disrupt access to cloud services.
- Compliance Violations: Failure to adhere to regulatory requirements.
Risk Assessment Methodology
- Identify Assets: List all critical assets in your cloud environment.
- Identify Threats: Identify potential threats to each asset.
- Assess Vulnerabilities: Determine vulnerabilities that could be exploited by threats.
- Evaluate Impact: Assess the potential impact of each threat on the asset.
- Calculate Risk: Calculate the risk based on the likelihood and impact of each threat.
- Mitigation: Implement measures to mitigate identified risks.
Cloud Security Alliance Self Assessment
The Cloud Security Alliance (CSA) provides tools and frameworks to help organizations conduct self-assessments of their cloud security posture.
CSA STAR Self-Assessment
The CSA Security, Trust, and Assurance Registry (STAR) self-assessment allows organizations to document their security controls and demonstrate compliance with CSA best practices.
Steps for CSA STAR Self-Assessment
- Download the CSA CAIQ: The Consensus Assessments Initiative Questionnaire (CAIQ) provides a standardized framework for assessing cloud security.
- Complete the Questionnaire: Provide detailed responses to the CAIQ questions.
- Submit to CSA STAR: Submit the completed questionnaire to the CSA STAR registry.
- Review and Update: Regularly review and update the self-assessment to reflect changes in your cloud environment.
Cloud Security Assessment Report
A cloud security assessment report documents the findings of the assessment, providing a comprehensive overview of the security posture and recommendations for improvement.
Key Components of a Cloud Security Assessment Report:
- Executive Summary: Overview of the assessment objectives, methodology, and key findings.
- Detailed Findings: In-depth analysis of identified vulnerabilities and security controls.
- Risk Assessment: Evaluation of risks based on the likelihood and impact of identified threats.
- Recommendations: Actionable steps to address identified risks and improve security posture.
- Appendices: Supporting documentation, such as questionnaires, configuration details, and tool outputs.
Cloud Security Assessment Tools
Various tools can assist in conducting a thorough cloud security assessment by automating data collection, analysis, and reporting.
Popular Cloud Security Assessment Tools:
- AWS Trusted Advisor: Provides real-time recommendations to help you follow AWS best practices.
- Azure Security Center: Offers unified security management and advanced threat protection.
- CloudSploit: Monitors cloud environments for security risks and compliance violations.
- Nessus: Conducts vulnerability assessments to identify security weaknesses.
- CloudHealth: Provides cloud security and compliance management.
Cloud Application Security Assessment
A cloud application security assessment focuses on evaluating the security of applications hosted in the cloud, ensuring they are protected against potential threats.
Steps for Cloud Application Security Assessment:
- Identify Applications: List all cloud-hosted applications to be assessed.
- Threat Modeling: Identify potential threats and vulnerabilities for each application.
- Security Testing: Conduct security tests, such as penetration testing and code reviews.
- Access Control Review: Evaluate access controls and permissions for each application.
- Data Protection: Assess encryption and data protection measures.
- Compliance Check: Ensure applications comply with relevant regulatory requirements.
Cloud Infrastructure Security Posture Assessment
A cloud infrastructure security posture assessment evaluates the overall security of your cloud infrastructure, including networks, servers, and storage.
Key Areas of Focus:
- Network Security: Assess firewall configurations, network segmentation, and access controls.
- Server Security: Evaluate server configurations, patch management, and security policies.
- Storage Security: Ensure data storage solutions are encrypted and access-controlled.
- Monitoring and Logging: Review monitoring and logging practices to detect and respond to security incidents.
- Compliance: Verify adherence to regulatory standards and industry best practices.
Cloud SaaS Security Assessment
A cloud SaaS security assessment evaluates the security of Software as a Service (SaaS) applications, ensuring they are secure and compliant with industry standards.
Steps for Cloud SaaS Security Assessment:
- Identify SaaS Applications: List all SaaS applications used by the organization.
- Vendor Assessment: Evaluate the security practices of SaaS providers.
- Access Control Review: Assess user access controls and permissions.
- Data Protection: Ensure data is encrypted and protected in transit and at rest.
- Compliance Check: Verify SaaS applications comply with relevant regulatory requirements.
- Incident Response: Assess the incident detection and response capabilities of SaaS providers.
Cloud Security Assessment Checklist
A cloud security assessment checklist provides a structured approach to ensure all aspects of cloud security are evaluated.
Example Cloud Security Assessment Checklist:
- Preparation:
- Define assessment scope and objectives.
- Gather relevant documentation and tools.
- Data Collection:
- Complete cloud security assessment questionnaire.
- Gather configuration and access control details.
- Security Controls Evaluation:
- Assess identity and access management.
- Review data protection measures.
- Evaluate network security configurations.
- Compliance Verification:
- Check adherence to regulatory requirements.
- Ensure compliance with industry standards.
- Risk Assessment:
- Identify potential threats and vulnerabilities.
- Evaluate the impact and likelihood of risks.
- Reporting:
- Document findings in a cloud security assessment report.
- Provide actionable recommendations for improvement.
- Follow-Up:
- Monitor the implementation of recommendations.
- Conduct periodic reassessments.
Cloud Security Assessment Framework
A cloud security assessment framework provides a structured approach to evaluating the security posture of cloud environments, ensuring a comprehensive and consistent assessment process.
Key Components of a Cloud Security Assessment Framework:
- Scope Definition: Define the scope and objectives of the assessment.
- Methodology: Establish the assessment methodology, including data collection, analysis, and reporting.
- Tools and Techniques: Identify the tools and techniques to be used for the assessment.
- Evaluation Criteria: Define the criteria for evaluating security controls and compliance.
- Reporting and Recommendations: Document findings and provide actionable recommendations.
Cloud Security Assessment Methodology
A robust cloud security assessment methodology ensures a thorough evaluation of cloud environments, covering all aspects of security.
Steps in a Cloud Security Assessment Methodology:
- Planning and Preparation:
- Define the assessment scope and objectives.
- Identify stakeholders and gather necessary documentation.
- Data Collection:
- Use questionnaires, tools, and interviews to gather information.
- Collect configuration details, access controls, and security policies.
- Risk Assessment:
- Identify potential threats and vulnerabilities.
- Evaluate the impact and likelihood of risks.
- Security Controls Evaluation:
- Assess the effectiveness of security controls.
- Verify compliance with regulatory requirements.
- Analysis and Evaluation:
- Analyze the collected data to identify security gaps.
- Compare findings against best practices and standards.
- Reporting:
- Document findings in a comprehensive cloud security assessment report.
- Provide actionable recommendations for improvement.
- Follow-Up:
- Monitor the implementation of recommendations.
- Conduct periodic reassessments to ensure continuous improvement.
Conclusion
Conducting a comprehensive cloud security assessment is essential for ensuring the security and compliance of your cloud environment. By leveraging tools, methodologies, and best practices, you can identify vulnerabilities, mitigate risks, and enhance your overall security posture. Whether you are assessing AWS, Azure, or other cloud platforms, following a structured approach and utilizing the right tools can help you achieve robust protection for your cloud assets.
Embrace the power of cloud security assessments to safeguard your cloud environment, ensure compliance, and achieve peace of mind in the ever-evolving landscape of cloud computing.
